How AI Threat Detection Is Transforming Enterprise Cybersecurity
Enterprise cybersecurity is facing a critical turning point. As digital ecosystems grow more complex, so do the threats that target them. From advanced phishing campaigns to AI-generated malware, attackers are evolving faster than legacy defenses can keep up. Conventional signature-based systems and manual threat monitoring are no longer enough. They react, rather than predict.
That’s where AI comes in. Artificial intelligence isn’t just another tool; it’s reshaping how enterprises detect, analyze, and respond to threats. With real-time pattern recognition, anomaly detection, and behavioral analysis, AI brings a proactive edge to modern cybersecurity.
The Growing Complexity of Enterprise Threats
Modern enterprises are under constant siege, and the threat landscape isn’t just growing, it’s evolving faster than most security teams can keep up.
-
Hybrid Work Models
With employees connecting from multiple locations and devices, networks are more exposed than ever. Every remote endpoint becomes a potential entryway for attackers.
-
Cloud and Multi-Cloud Environments
As organizations migrate critical workloads to public and private clouds, they often struggle to maintain consistent security controls, leaving visibility gaps and misconfiguration risks.
-
Internet of Things (IoT)
Billions of smart devices are now connected to enterprise ecosystems. Most lack strong security protocols, making them easy targets for lateral movement or botnet recruitment.
-
Real-Time, Automated Threats
Attackers are using AI too. From AI-generated phishing to self-morphing malware, threat actors now operate at machine speed, outpacing traditional security tools.
What Is AI-Driven Threat Detection?
For CISOs, AI-driven threat detection isn’t just a buzzword; it’s becoming a mission-critical component of enterprise cybersecurity. At its core, AI threat detection refers to the use of machine learning and advanced data modeling to identify malicious behavior in real-time. Unlike traditional signature-based methods that only detect known threats, AI learns and evolves with your network, flagging anomalies and suspicious patterns before they escalate.
The shift is simple but significant: legacy systems react. AI systems predict. With behavior modeling, machine learning algorithms continuously analyze network activity, adapt to user behavior, and surface potential threats that human analysts or outdated tools would miss. That means faster detection, fewer false positives, and a proactive security posture, not a reactive one.
For CISOs, this translates into more than just automation. It’s about gaining visibility into blind spots, scaling threat detection across hybrid infrastructures, and freeing up security teams to focus on strategic tasks.
Key Benefits of AI Threat Detection in Enterprise Security: What CISOs Are Looking For
In today’s high-stakes threat landscape, CISOs don’t just want more tools; they need better, smarter ones. AI-powered threat detection offers exactly that by transforming how enterprise environments monitor, analyze, and respond to risks at scale.
Here’s what forward-thinking CISOs prioritize:
-
Faster Detection & Response
Speed is everything. AI enables real-time monitoring that quickly identifies unusual activity, allowing teams to act before damage is done.
-
Reduction in False Positives
Security teams are overloaded. Machine learning algorithms learn and improve over time, drastically reducing noise and surfacing only what truly matters.
-
Scalable Infrastructure Protection
Whether it's a hybrid cloud, on-prem, or remote setup, AI can scale alongside the infrastructure, providing centralized oversight across all endpoints.
-
Predictive Threat Intelligence
Beyond alerts, AI helps anticipate where attacks might happen next, enabling proactive defense strategies that reduce risk exposure.
AI Threat Detection in Action: What CISOs Need
According to Darktrace's State of AI in Cybersecurity report, 78% of CISOs believe AI is already influencing cybersecurity in a major way. As threats evolve, enterprise leaders are turning to AI to stay ahead. It’s not just a future trend, it’s a present necessity for protection.
The digital perimeter has expanded beyond firewalls and adversaries are moving faster than ever. What CISOs want isn’t more alerts; they want precision, speed, and context. AI delivers on that promise through AI threat detection that directly addresses enterprise risk.
Insider Threat Detection
AI models analyze user behavior to detect subtle deviations, like abnormal login times or file access patterns, before they escalate into breaches.
Endpoint Security & Behavioral Analysis
With AI, CISOs gain real-time visibility across all endpoints, using behavioral baselines to flag anomalies instantly, even on zero-day exploits.
Cloud Infrastructure Monitoring
Cloud-native AI threat detection identifies misconfigurations, privilege escalations, and unusual API calls, critical in dynamic multi-cloud environments.
Advanced Phishing & Fraud Detection
Machine learning scans email patterns, domain spoofing tactics, and sender behavior to block phishing attempts that bypass traditional filters.
As threats grow in complexity, AI doesn’t just detect faster, it learns faster. For CISOs, that’s the edge: proactive threat prevention without drowning in noise. And for cybersecurity vendors, aligning solutions with these high-impact AI use cases is how you earn trust and contracts.
Considerations and Challenges for CISOs in Adopting AI Threat Detection
While AI threat detection is revolutionizing cybersecurity, CISOs face unique challenges when integrating these advanced technologies into enterprise environments.
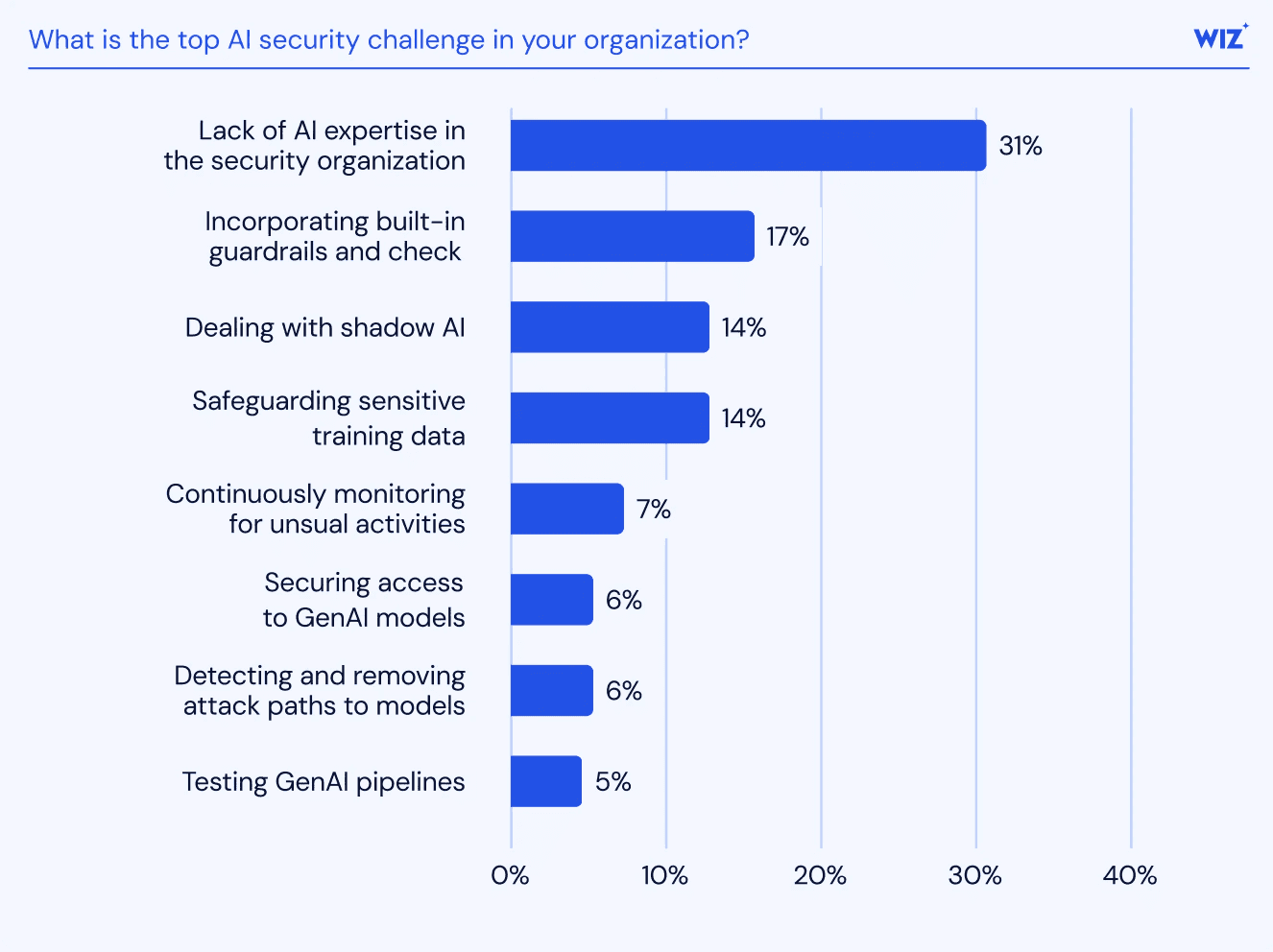
Top AI security challenges according to results from the AI Readiness Report
Here's what to consider:
Data Privacy & AI Bias
AI-driven threat detection systems often require access to sensitive user data. Ensuring compliance with privacy regulations like GDPR and HIPAA, while addressing potential biases in machine learning models, is crucial for maintaining trust and accuracy.
Integration with Existing Security Stacks
Enterprises already rely on a complex web of security tools. Incorporating AI-powered threat detection into SIEM, SOAR, and endpoint platforms requires seamless integration without disrupting real-time operations.
Skills Gaps & Training Needs
Advanced threat detection with AI demands new skill sets. Upskilling internal teams or relying on third-party vendors becomes essential for operational success.
Compliance & Governance
As cybersecurity threat detection evolves, so do compliance requirements. CISOs must ensure their AI for threat detection strategies align with industry standards and reporting protocols.
The Future of AI Threat Detection: Why CISOs Can’t Afford to Wait
For CISOs, AI threat detection is no longer a future-forward experiment; it’s a business imperative. As threat actors evolve faster than legacy systems can respond, the need for advanced threat detection powered by AI is pressing.
At the RSA Conference 2025, AI-driven threat detection took center stage as CISOs explored smarter, faster ways to secure enterprise systems. With evolving attack surfaces, cybersecurity leaders are turning to AI to reduce false positives, accelerate response times, and stay ahead of threats.
Autonomous response and adaptive AI are giving security leaders real-time visibility and decision support. Whether it's identifying behavioral anomalies or launching automated threat detection protocols, AI doesn’t sleep and in today’s attack climate, that’s non-negotiable.
- AI-powered threat detection and prevention tools now integrate with XDR, SIEM, and SOAR platforms to streamline response.
- AI-driven threat detection and response reduce false positives while prioritizing real risks.
- Predictive threat intelligence paired with machine learning gives security teams a proactive edge.
What’s at stake? Everything. Compliance, trust, and business continuity depend on a CISO’s ability to act fast and accurately. That’s why AI for threat detection isn’t optional anymore; it’s foundational.
Execweb’s Role in Enabling Secure AI Adoption for Enterprise Cybersecurity
The surge in automated threat detection, AI-powered threat intelligence, and real-time threat detection means cybersecurity decisions are more complex than ever. Execweb bridges this gap by connecting CISOs directly with AI-driven threat detection vendors that are vetted, credible, and built to scale.
With EXECWEB, enterprises gain more than vendor options; they gain a strategic ally that understands the complexity of AI threat detection, compliance, and budget realities. Execweb connects CISOs with trusted, vetted cybersecurity solutions while giving vendors direct access to decision-makers.
Conclusion: AI As The Backbone of Future-Ready Security
From AI-powered threat detection and prevention to predictive threat intelligence, such technologies give security leaders the edge they need. But tools alone aren’t enough. It takes a strategic mindset, one that values automated threat detection, fast decision-making, and constant innovation.
This is where Execweb steps in, curating trusted partnerships between cybersecurity vendors and forward-thinking CISOs. If you’re ready to modernize your defenses with AI-driven threat detection, start with the right network.
Let’s connect. Discover vetted solutions, peer insights, and innovation tailored to your security mission, only at execweb.
- 28 views
- 0 comments









Comment