Key Considerations for Vendors When Designing Custom Cybersecurity Solutions
As businesses become more and more technologically oriented, a one-size-fits-all strategy simply isn’t enough. Different businesses have different needs, vulnerabilities, and regulation requirements. A hospital institution that handles sensitive patient data will prioritize securing medical records, but an e-commerce platform may prioritize protecting credit card information. These special vulnerabilities demand specific compliance regulations, as healthcare institutions might focus on locking down electronic health records to comply with HIPAA regulations, which demand privacy and security of patient information. At the same time, e-commerce platforms might prioritize protecting credit card details and adhere to PCI DSS, a global standard for securing cardholder data.
This is where custom cybersecurity solutions come in, offering a tailored approach to address specific cybersecurity challenges. However, designing effective custom cybersecurity solutions requires careful consideration from vendors. This article dives deep into the key areas vendors need to focus on when developing these custom solutions.
Understanding the Client Needs:
Designing effective custom cybersecurity solutions requires a deep dive into the client's specific security environment. This starts with understanding what companies need cybersecurity and how you can cater to them.
Next comes an examination of the client's current security setup. This includes all existing security such as the current cloud-based security, operating systems, applications used daily, and chosen data storage platforms. By meticulously going through the current infrastructure, vendors can identify any existing vulnerabilities or areas of improvement.
Compliance requirements are another point to take into consideration. Custom cybersecurity solutions must be designed with regulations in mind to ensure the client remains compliant and avoids fines and lawsuits.
Finally, no security strategy is complete without staying up to date with the threat landscape. Vendors who are designing customized cybersecurity need to understand the latest cyber attacks targeting the client's specific industry, as well as trends in the industry, allowing them to develop proactive defenses that are designed to tackle a multitude of cyberattacks.
Gathering Information:
Gathering information is crucial for developing custom cybersecurity solutions for a client's specific needs. Vendors who are designing customized cybersecurity solutions can achieve this by first interviewing key decision-makers like IT personnel, executives, and security officers to provide invaluable insights. By asking questions, vendors can understand the client's priorities and their budgetary limitations.
Check out this webinar to learn effective strategies on how security vendors can approach and connect with security practitioners.
Secondly, customized security questionnaires can be employed to gather specific details about the client's existing cybersecurity. These questionnaires should ask about the client's security policies and procedures, as well as any past security cyberattacks that may have occurred. Understanding a client's current cybersecurity setup allows vendors to identify areas for improvement and helps them customize their solutions
Building a Cybersecurity Strategy:
Once the client's needs are defined and understood, vendors can start designing the perfect custom cybersecurity solutions for them. Here are some services to add to your custom solutions:
1. Endpoint Security:
Endpoint security is one of the most important parts of any cybersecurity strategy. Endpoints, such as laptops, tablets, and mobile phones, are entry points for security threats. To protect these endpoints, organizations need to implement firewalls, content filtering, unified threat management, and other advanced security measures. By securing these entry points, organizations can establish the first line of defense against potential cyberattacks.
2. Access Control:
With the increase in IoT devices and mobile users, organizations face new challenges in securing their networks. Network access control solutions enforce security across wired and wireless networks. This service makes sure that only authorized devices and users can access the network, reducing the risk of any sort of unauthorized access and potential security breaches. Implementing network access control measures is crucial in today's interconnected world to prevent cyber attacks.
3. Data Protection:
When designing custom cybersecurity solutions vendors should make protecting data their utmost priority. Effective governance, visibility, control, encryption, and structured monitoring and management are key considerations in data security. Organizations need to protect their data's confidentiality, integrity, and availability. This involves implementing measures such as data encryption, access controls, and regular data backups.
4. Cloud Security:
For top-notch protection, custom cybersecurity solutions should extend beyond firewalls. Cloud security tools act like extra guards for your online data. Imagine watchers constantly monitoring your cloud storage for suspicious activity, gatekeepers verifying every user accessing your information, and checkup tools finding weak spots hackers might target. By incorporating these cloud-specific features such as cloud workload protection platforms, cloud access security brokers, and cloud security posture management, vendors can design custom cybersecurity solutions that keep your valuable data safe in the cloud, from all angles.
If you are thinking of introducing your services to the business world. Check out this blog that details how to sell cybersecurity products and services to all-sized businesses.
Implementing the Custom Solution:
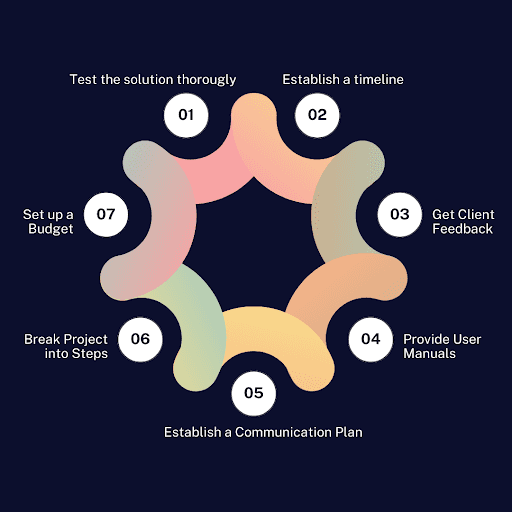
Once you have created the cybersecurity solution design, the next step is to successfully implement it. First, figure out how long it will take, how much it will cost, and how you'll stay in touch with the client throughout the process. This establishes a clear timeline, budget, and communication plan to ensure both client expectations and project goals are met.
Next, break the project into smaller steps and get the client's feedback often. After completing each step, you can present it to the client and get their feedback. This allows them to see the progress, confirm it aligns with their vision, and suggest any adjustments before moving on to the next stage.
Before launching the solution, test it thoroughly to find and fix any weak spots. Testing is like running the solution through an obstacle course, exposing any weak spots or bugs that could cause problems later. This might involve simulating real-world scenarios, pushing the solution to its limits to see how it handles high volumes of data or unexpected user behavior.
Finally, the key to successfully implementing a complex solution isn't just the technology itself, but ensuring that users can use it to its full potential. This is where clear, comprehensive user manuals and training programs come in. Detailed guides, written in an easy-to-understand manner, break down complicated functions into manageable steps for users.
Furthermore, providing training sessions on using the solution can empower the client's team by providing hands-on experience in its operation and maintenance.
Looking to Sell Your Custom Cybersecurity Solutions?
As discussed in this blog, creating custom solutions is essential for clients to get all-encompassing security. However, identifying potential clients who need them remains a key challenge for vendors.
This is where Execweb steps in, we have a CISO Executive Network consisting of Fortune 500 CISOs and top-level executives actively in search of vendors who supply innovative cybersecurity services.
Execweb connects you with these CISOs so that you can sell your services or get feedback on your custom services and products. Simply visit our website and sign up to get in touch with CISOs.








Comment