How Do Managed Cybersecurity Services Work?
In today's digital landscape, cybersecurity managed services are no longer just a priority for large enterprises. Small and medium-sized businesses (SMBs) are increasingly targeted due to perceived vulnerabilities, making managed cybersecurity services essential across the board. Many organizations find it challenging to maintain robust in-house security measures as cyber threats evolve in complexity and frequency. This is where Managed Cybersecurity Services come into play, offering specialized protection tailored to your business needs.
This blog guides you through what managed cybersecurity entails, why it’s crucial for businesses of all sizes, and how partnering with a managed cybersecurity services provider can shield your organization from ever-evolving cyber threats.
You may also want to read: Cybersecurity for Startups.
What Are Managed Cybersecurity Services?
Managed Cybersecurity Services involve outsourcing your organization's cybersecurity functions to specialized providers known as Managed Security Service Providers (MSSPs). These services encompass a range of security measures, including threat detection, incident response, compliance management, and continuous monitoring.
With fully managed cybersecurity, businesses benefit from a comprehensive approach where every layer, from endpoint to cloud, is monitored and secured. This frees up internal teams to focus on core operations while knowing their infrastructure is under professional watch.
Key Components of Managed Cybersecurity Services
A fully managed cybersecurity setup provides end-to-end protection. It includes:
- 24/7 Monitoring and Threat Detection: Continuous surveillance of your network to identify and mitigate threats in real-time.
- Incident Response and Recovery: Quick response to security incidents to minimize damage and ensure swift recovery.
- Compliance Management: Assistance in adhering to industry regulations and standards, such as GDPR, HIPAA, and PCI DSS.
- Security Assessments and Audits: Regular evaluations to identify vulnerabilities and strengthen defenses.
- Managed Detection and Response (MDR): Combines advanced technology with human expertise to detect and respond to threats proactively.
- Custom Security Architecture: Whether on-premises or in the cloud, managed cyber services tailor solutions to your business model and risk profile.
These managed cybersecurity solutions are ideal for SMBs that need enterprise-level security without the cost of an internal team.
Benefits of Managed Cybersecurity Services
1. Eliminates Alert Fatigue and Overload
In-house IT teams can get overwhelmed by endless security alerts. MSSPs filter out false positives and only escalate real threats, so your team can focus on core tasks without constant interruptions.
2. Improves Business Focus and Efficiency
By offloading security operations, your internal team can focus on innovation and growth. Security becomes one less thing to worry about, boosting both morale and productivity.
3. Reduces the Complexity of Managing Security Tools
Companies often juggle too many security tools that don’t integrate well. A managed cybersecurity services provider simplifies this by unifying tools under one platform with centralized management and reporting.
4. Supports Scalable IT Operations
As your company expands, so do your cybersecurity needs. MSSPs provide scalable protection that grows alongside your IT infrastructure, without needing constant manual upgrades or internal hiring.
5. Cost-Effective Cybersecurity Management
Instead of investing heavily in building and maintaining an in-house security team and infrastructure, managed cybersecurity services offer a predictable, subscription-based pricing model.
Working Models Of Managed Security Services
There are two models of managed cybersecurity services:
1. Fully Managed Security Services
This hands-off model is ideal for small to mid-sized businesses or those lacking a dedicated internal security team. A managed cybersecurity service provider takes full responsibility for:
- 24/7 threat monitoring and management
- Endpoint detection and response (EDR)
- Threat intelligence and analytics
- Configuration and patch management
- Compliance reporting
- Incident detection, response, and remediation
Why choose this model?
You get enterprise-level protection without the cost and complexity of building an internal security operations center (SOC). The MSSP acts like your outsourced cybersecurity department.
This model is especially valuable in industries with heavy compliance needs, such as healthcare, finance, and e-commerce.
2. Co-Managed Security Services (Hybrid Model)
Many medium to large enterprises opt for this approach, where the internal IT/security team collaborates with an MSSP to divide responsibilities.
- Internal team handles day-to-day IT and lower-risk security tasks.
- MSSP focuses on advanced threat detection, compliance, and incident response.
Benefits of Co-Managed Cybersecurity:
- Greater visibility and control over your infrastructure
- Expert support without giving up internal oversight
- Scalability – MSSPs can handle extra load when needed
- Training and knowledge-sharing for internal teams
This model works great for organizations with some cybersecurity maturity but who need backup for monitoring, compliance, or more advanced threats.
How Can Managed IT Services Improve Cybersecurity?
You may be wondering, how can managed IT services improve cybersecurity? The answer lies in their proactive, layered approach. A reputable managed cybersecurity services provider delivers more than just monitoring — they offer:
- Holistic visibility across your digital environment.
- Automated threat response.
- Strategic guidance from certified experts.
- Reduced overhead costs compared to in-house teams.
By partnering with a managed cybersecurity solution provider, businesses gain access to enterprise-level security tools and intelligence, helping them stay ahead of threats and stay compliant.
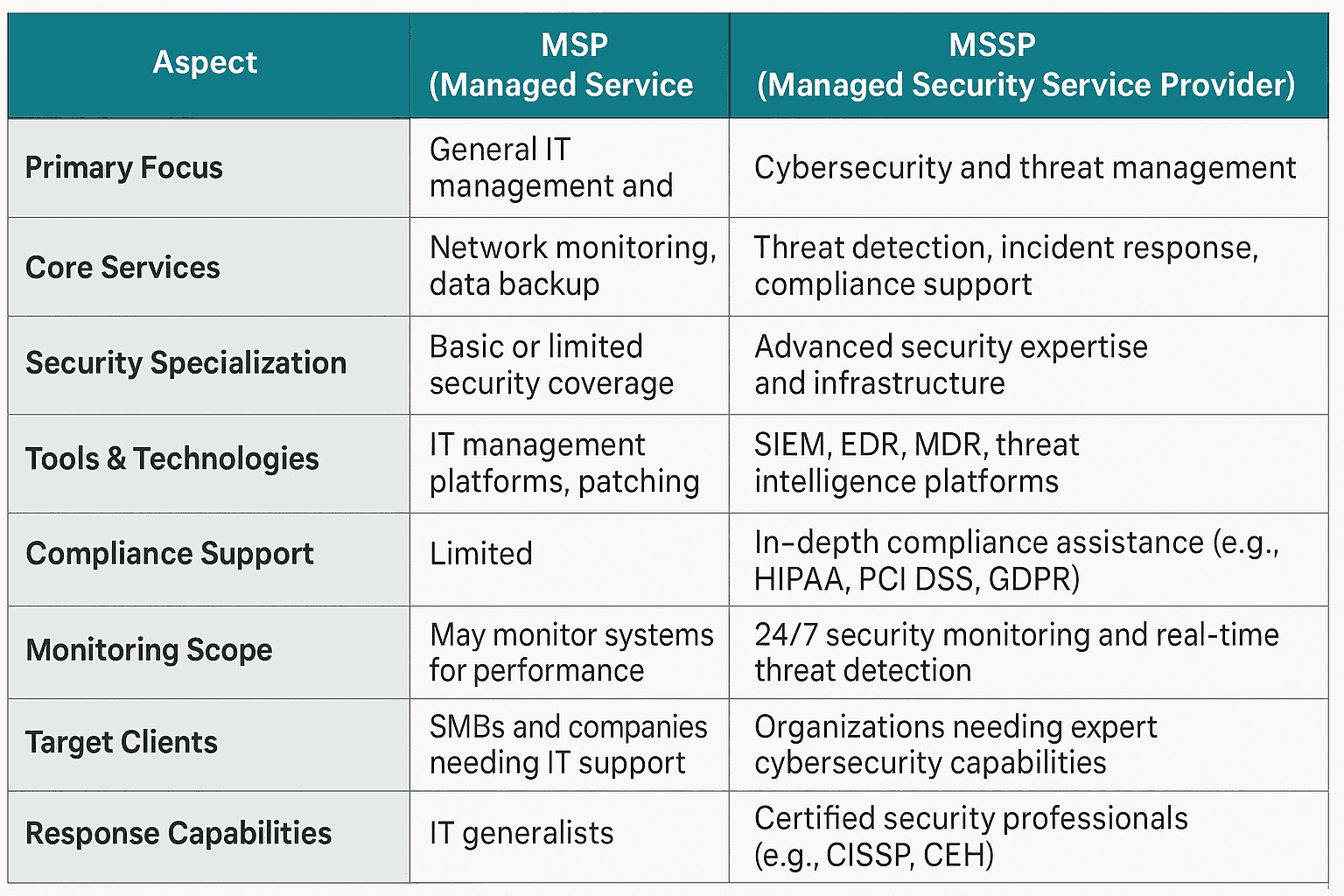
MSP vs. MSSP: Understanding the Difference
In the world of outsourced IT and cybersecurity, it’s essential to understand the difference between MSP and MSSP, as both serve different yet often complementary roles in your technology stack.
MSP (Managed Service Provider): Focuses on managing IT services, such as network management, data backup, and software updates.
MSSP (Managed Security Service Provider): Specializes in providing security services, including threat monitoring, incident response, and compliance management.
By choosing the right managed cybersecurity services provider, businesses can ensure they’re not just supported but truly protected.
Why Managed Cybersecurity Services Are Crucial for Organizations
Many organizations today face growing cybersecurity challenges that are difficult to tackle alone. The financial burden of building advanced security infrastructure is significant, especially for startups and small-to-medium businesses. Additionally, finding and retaining skilled cybersecurity professionals is increasingly difficult due to a global talent shortage.
Beyond cost and talent constraints, businesses often struggle to maintain security operations outside regular business hours, creating gaps that cybercriminals can exploit. This is where partnering with Managed Cybersecurity Services Providers (MSSPs) becomes a strategic move. MSSPs offer cost-effective expertise, 24/7 monitoring, and advanced security technologies that would be prohibitively expensive or complex for many companies to manage internally.
Here’s how MSSPs help safeguard your business:
1. Penetration Testing
MSSPs perform penetration testing to identify vulnerabilities in your systems and devices. Whether as a one-time or ongoing service, these tests reveal weak points and help prioritize necessary security upgrades, ensuring your defenses stay robust.
2. Threat Monitoring & Management
With continuous monitoring, MSSPs analyze security data in real-time to detect suspicious network activity or signs of compromise. Their teams use sophisticated tools to identify and neutralize threats before they can cause damage.
3. Security Intelligence
MSSPs bring broad experience from serving diverse clients and employ threat intelligence to anticipate emerging cyber risks like ransomware and zero-day exploits. This proactive approach enhances your security posture beyond traditional defenses.
4. Incident Response
In case of a breach, MSSPs respond quickly to contain the attack and remediate damage. Their expertise accelerates recovery, minimizing downtime and preventing prolonged disruption to critical business operations.
For companies seeking to strengthen security without overwhelming resources, cyber managed service offer a reliable way to outsource complex security tasks.
Choosing the Right Managed Cybersecurity Service Provider
When selecting a Managed Cybersecurity Services Provider, consider the following factors:
- Experience and Expertise: Evaluate their track record and the qualifications of their security professionals.
- Range of Services: Ensure they offer comprehensive services that align with your business needs.
- Customization: Look for providers that can tailor their services to your specific requirements.
- Compliance Support: Verify their ability to assist with regulatory compliance relevant to your industry.
- Customer Support: Assess their responsiveness and availability to address your concerns promptly.
Future Trends in Managed Cybersecurity
- Artificial Intelligence (AI) and Machine Learning (ML): Enhancing threat detection and response capabilities through predictive analytics and AI.
- Zero Trust Security Models: Implementing strict access controls to minimize the risk of internal and external threats.
- Cloud Security: Securing data and applications in cloud environments as businesses increasingly adopt cloud solutions.
- Regulatory Changes: Staying abreast of evolving compliance requirements to ensure ongoing adherence.
Where MSSPs and Organizations Find Each Other
If you’re looking for trusted guidance and access to experienced cybersecurity leaders who understand the challenges your organization faces, Execweb can be a valuable resource. Whether you’re an MSSP looking to connect with organizations in need of managed cybersecurity services or a business searching for the right MSSP to protect your digital assets, Execweb brings both sides together. It helps providers find clients who need their expertise, and helps organizations find trusted partners to secure their operations. Explore how Execweb can support your cybersecurity goals and help protect what matters most.
Conclusion
In an era where cyber threats are ever-present and increasingly sophisticated, Managed Cybersecurity Services offer a proactive and cost-effective solution for businesses seeking to protect their digital assets. By outsourcing security functions to specialized providers, organizations can benefit from expert knowledge, advanced technologies, and continuous monitoring while focusing on their core business objectives.
Whether you're a small business looking to enhance your security posture or a larger enterprise aiming to streamline your cybersecurity operations, partnering with a Managed Cybersecurity Services Provider can be a strategic move toward achieving robust and resilient security.
FAQs
1. How do managed security services work?
They monitor, detect, and respond to cyber threats on your behalf using expert teams and tools. This helps ensure 24/7 protection without needing an in-house security team.
2. What is the difference between MSP and MSSP?
MSPs manage general IT and networking needs, while MSSPs focus solely on cybersecurity, threat detection, and incident response.
3. What are managed services in cybersecurity?
Managed Services are outsourced services that handle businesses’ security operations like threat detection, incident response, and system monitoring.
4. How much do managed cybersecurity services cost?
Managed cybersecurity services typically cost between $1,000 to $10,000 per month. Small businesses may spend around $1,000–$3,000, while mid to large enterprises often require more advanced protection, pushing costs toward $10,000 or more.







Comment